Cybersecurity Operations
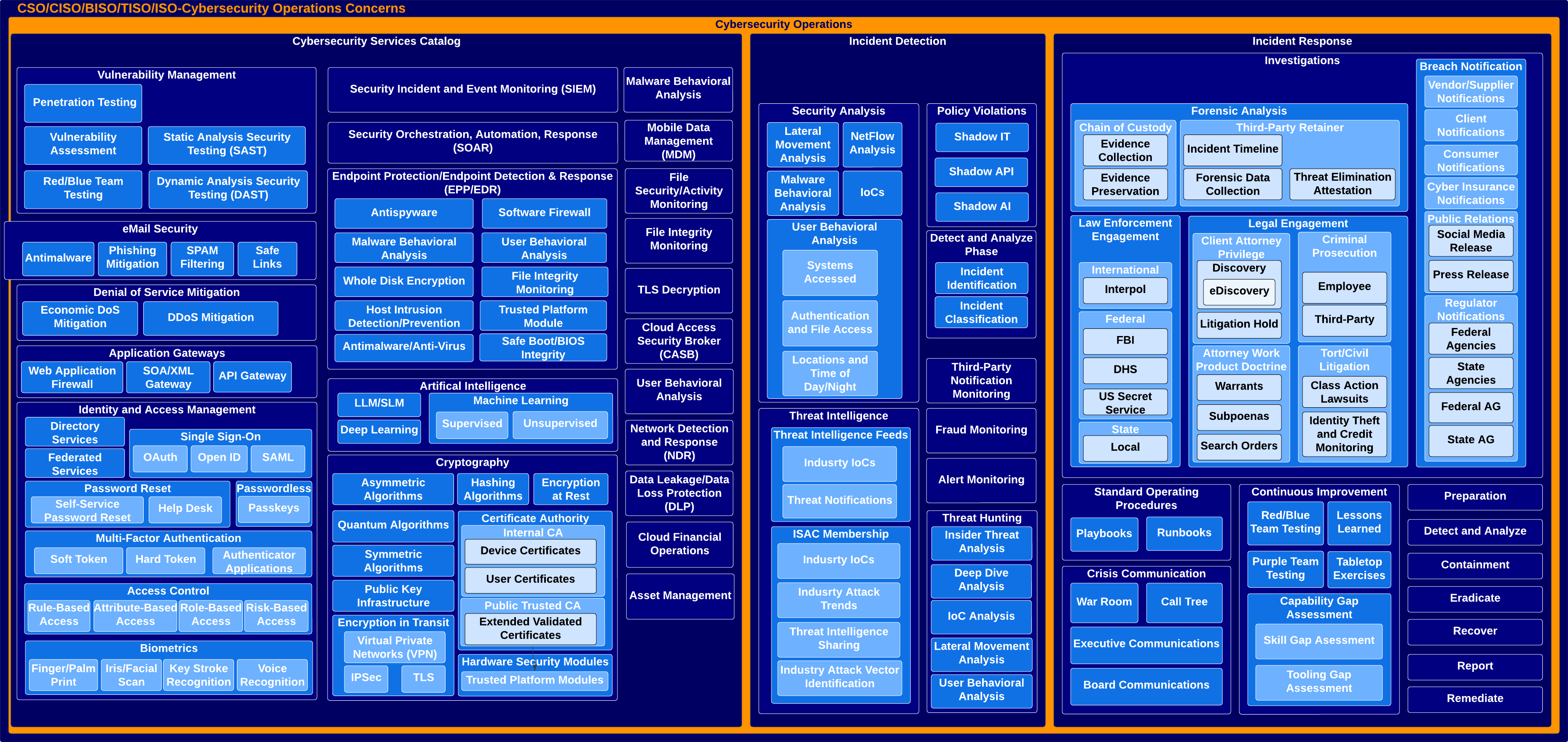
Continuing the conversation on cybersecurity leaders’ concerns is cybersecurity operations. This domain directly impacts a company and is divided into cybersecurity services catalog, incident detection, and incident response. This area of concern can lead to sleepless nights. The cybersecurity services catalog includes all the tools and services implemented via cybersecurity architecture to support the operating model of the cybersecurity program. Operators leverage them in a fusion center, cybersecurity operations center, or security operations center to detect incidents and enact incident response as needed. This might be considered where the rubber meets the road for a cybersecurity program. The cybersecurity services management architecture defines the cybersecurity services catalog. Tooling that is ineffective can lead to significant issues. A lack of labor resources can also lead to substantial problems, such as missed alerts and notifications with an active threat actor within an environment.
Anyone can use and modify this public domain document to meet their needs.
As a working cybersecurity professional, every attempt is made to separate professional and personal endeavors in a manner consistent with reducing conflicts of interest and maintaining ethics. Statements contained within this site are the explicit and implicit goals, objectives, endorsements, and educated opinion of the author of this site and not those of current or former employers.

