Enterprise Cybersecurity Architecture-Reference Architecture
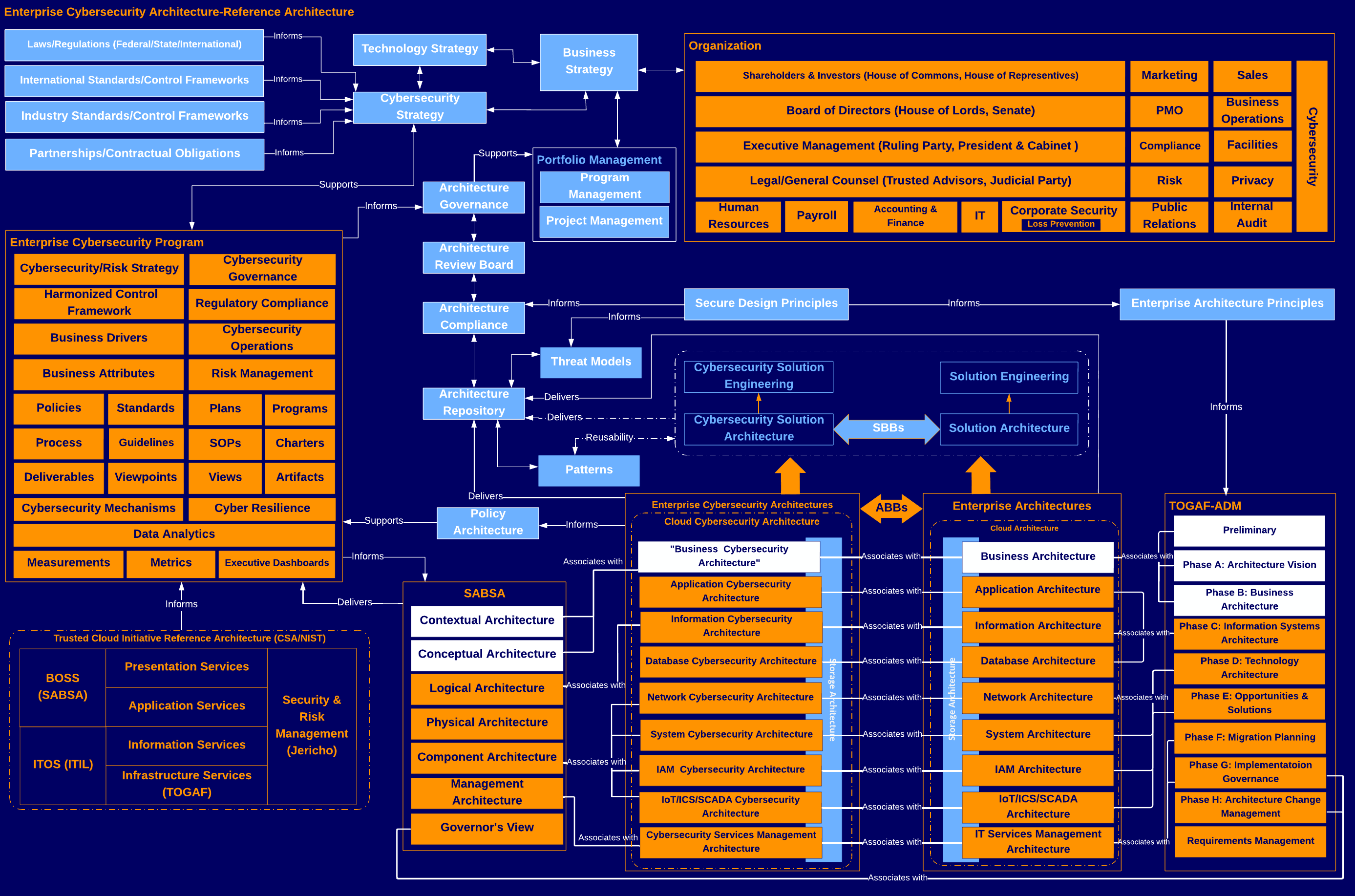
Every enterprise cybersecurity architecture must start somewhere. The reference architecture depicted here provides the initial basis for developing one for any organization. It is industry-agnostic and standards-focused, and it integrates TOGAF and SABSA. In addition, it is influenced by the Trusted Cloud Initiative Reference Architecture developed by the Cloud Security Alliance and NIST. This is not meant to be a rigid and set view. It can be adapted to other influences and architectural frameworks as needed or desired. It is merely a starting point and foundational.
The enterprise cybersecurity architecture reference architecture is cyclic/iterative and adaptable to agile methodology. It is not a bolt-on afterward perspective but one where various teams, top-down and bottom-up, work together to develop corporate and product-level technology deployments and platform ecosystems, whether on-premises, cloud, or hybrid.
Anyone can use this public domain document and modify it to suit their needs.
SABSA is the copyright and trademark of the SABSA Institute; all rights reserved.
TOGAF is the copyright and trademark of The Open Group; all rights reserved.
Enterprise Cybersecurity Architecture-Domain Mapping
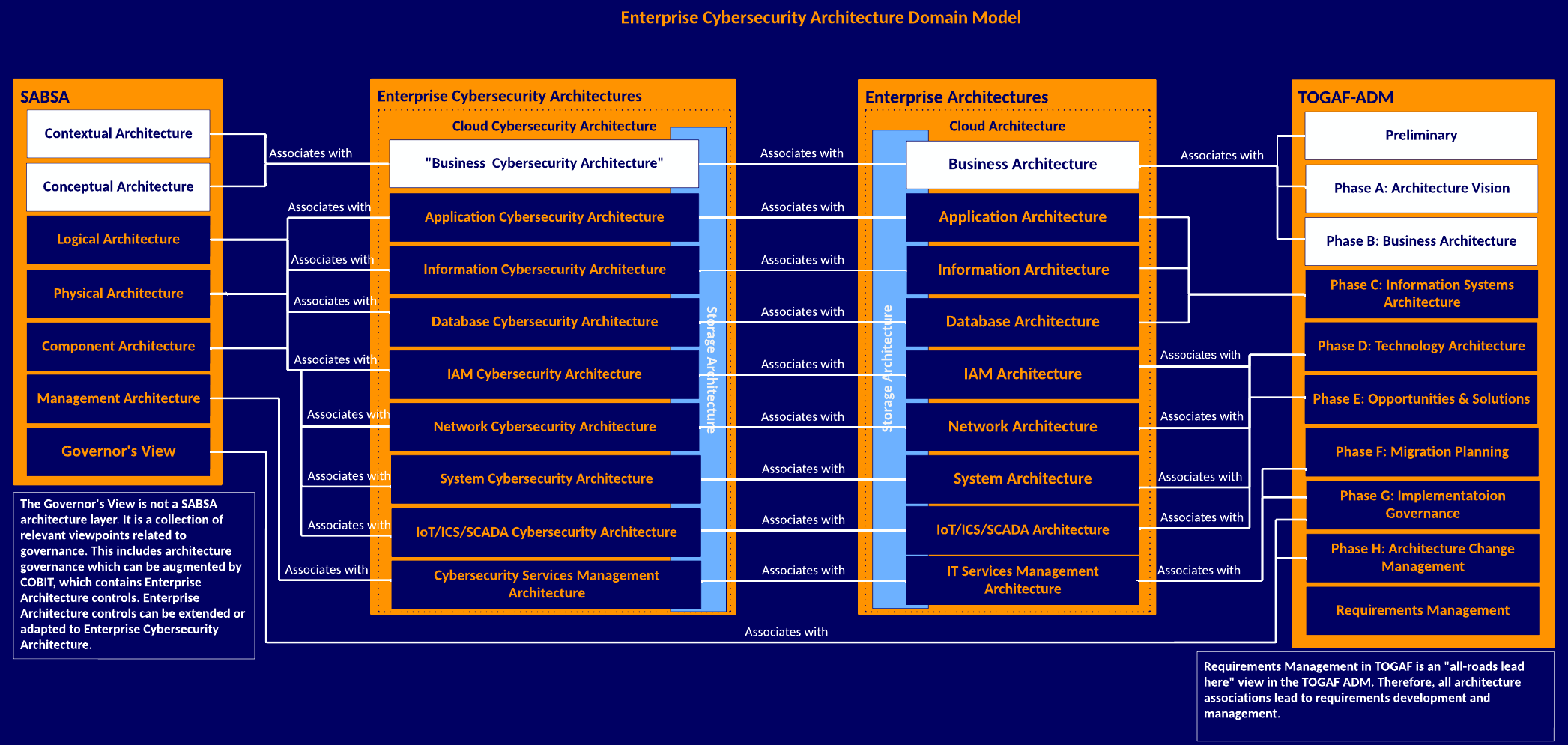
The enterprise cybersecurity architecture domain mapping focuses on the bottom right section of the enterprise cybersecurity architecture-reference architecture. To elaborate on the conversation, the domain mapping encapsulates the architecture domains within a cloud architecture domain within the higher-level enterprise architecture domain. Likewise, the cloud cybersecurity architecture domain encapsulates each cybersecurity architecture domain within the higher-level enterprise cybersecurity architecture domain.
This acknowledges that the architecture domains are agnostic to on-premises, cloud, and hybrid-based architectures regardless of the cloud service provider or whether an organization operates a private cloud. An organization with no cloud presence could remove the cloud domain encapsulation. However, an organization that is one hundred percent in the cloud would not remove the enterprise and cybersecurity architecture high-level domains because they are functionally foundational.
The domains are mapped to SABSA and the TOGAF ADM to provide associations to the various domain architectures being developed.
Anyone can use this public domain domain document and modify it to suit their needs.
SABSA is the copyright and trademark of the SABSA Institute; all rights reserved.
TOGAF is the copyright and trademark of the The Open Group; all rights reserved.
Enterprise Cybersecurity Architecture-Domain Mapping-Extended
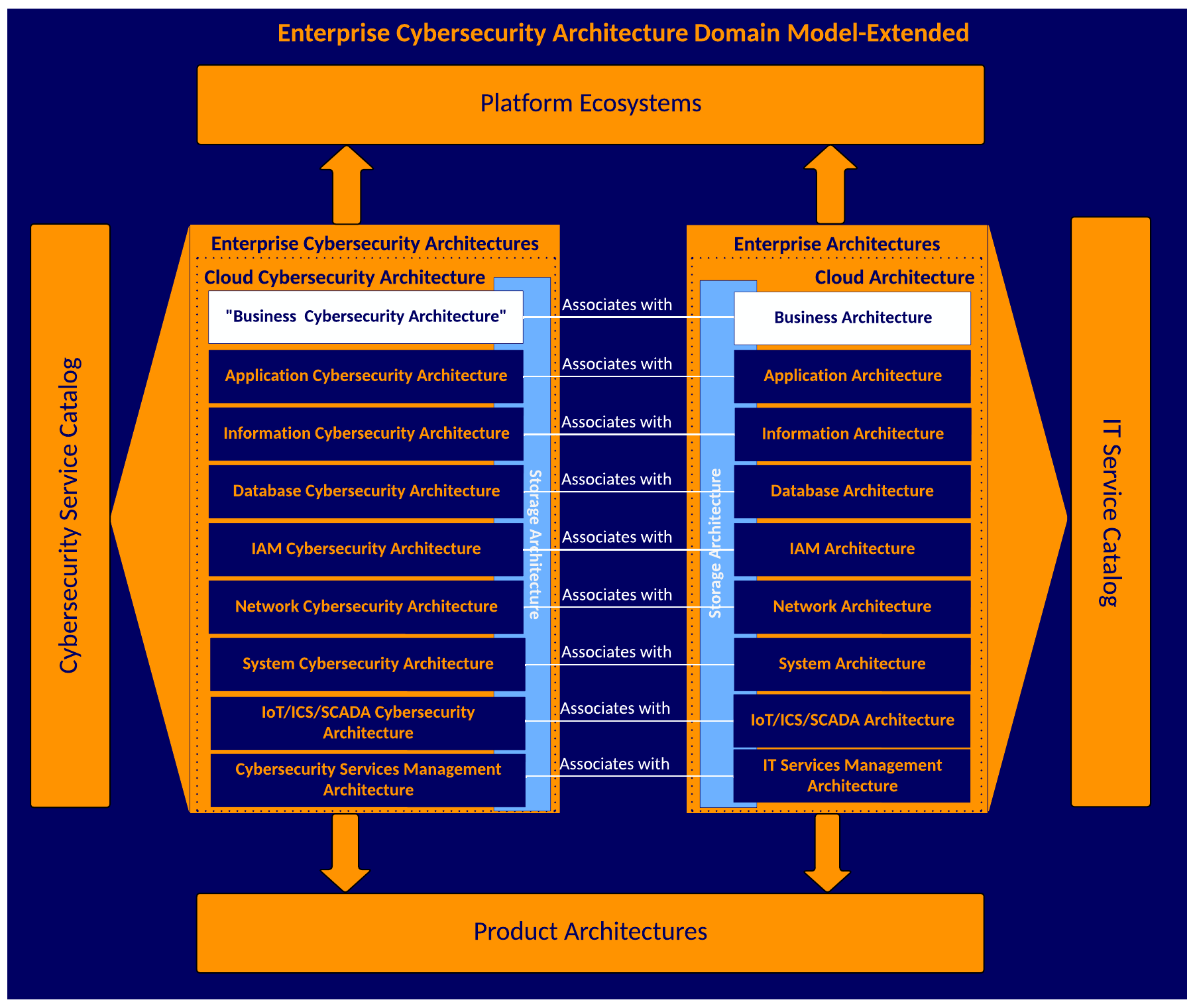
The enterprise cybersecurity architecture domain mapping was extended to show platform ecosystems and product architectures while noting the IT and cybersecurity service catalog views. This provides a directed view of where architecture leads, supports, and implements, whether on-premises, cloud, or hybrid.
Anyone can use this public domain document and modify it to suit their needs.
Enterprise Cybersecurity Paradigm-Reference Architecture
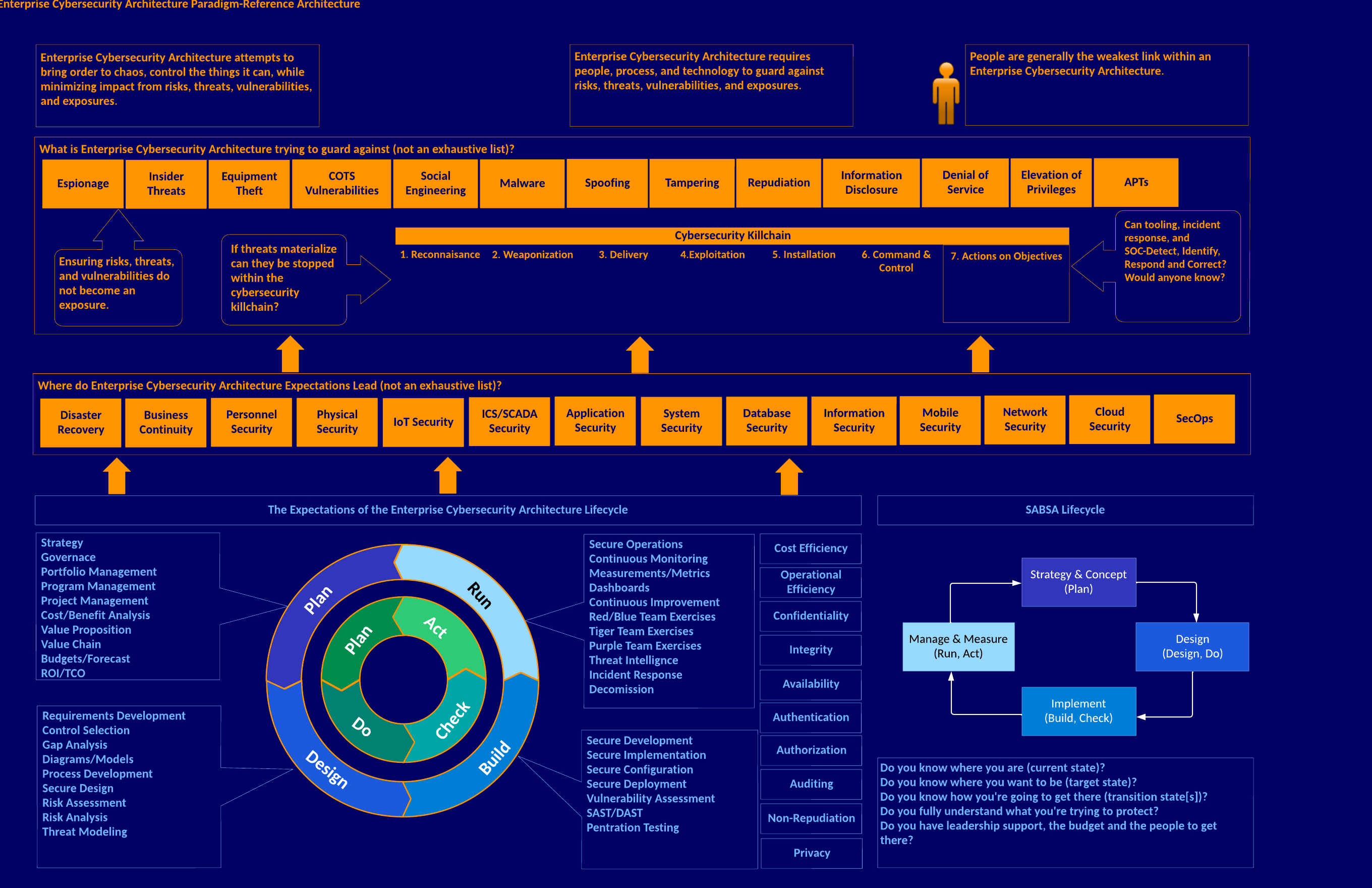
Every enterprise cybersecurity architecture follows a paradigm. The paradigm means a lifecycle is attached to the architecture, as the SABSA lifecycle notes. The lifecycle overlays with the familiar Plan, Do, Check, Act (PDCA) cycle (Deming or Shewhart cycle). This ties into or can overlay with the Plan, Design, Build, Run model and aligns with the conceptual perspective of the SABSA lifecycle.
The ECSA paradigm provides an industry-agnostic view of expectations within each area adaptable to rigid organizations or for looser, more agile-focused organizations, but the expectations remain the same. In addition, the ECSA paradigm leads to expectations regarding an organization’s areas of interest and the likely places to be protected.
Remember that the lifecycle ties into the current, target, and transition state architectures. This means integrating cybersecurity mechanisms and tooling, strategy, capability development, and architecture deployment, whether cloud, hybrid, or on-premises technology deployments, with portfolio, program, and project management.
Anyone can use this public domain document and modify it to suit their needs.
SABSA is the copyright and trademark of the SABSA Institute; all rights reserved.
Cybersecurity and Technology Operations Paradigm-Reference Architecture
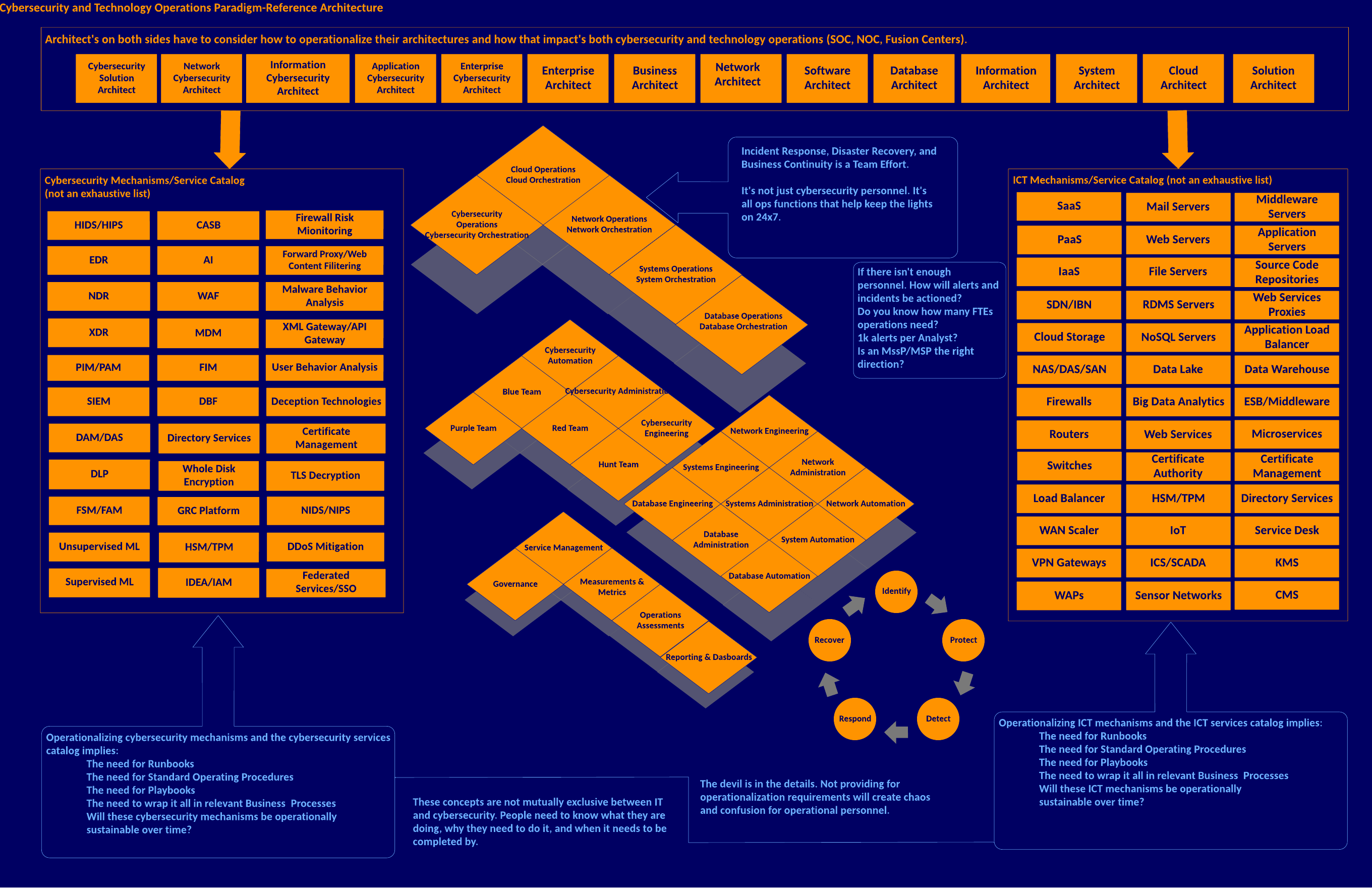
All technical architectures lead to operationalization. The Cybersecurity and Technical Operations Paradigm focuses attention on areas of operationalization, ensuring mutual inclusivity between IT and Cybersecurity. This is where the Cybersecurity Services Management and IT Management architectures lead.
An enterprise cybersecurity architecture that does not account for operations is wishful thinking and shelfware. All architectures must consider integrating CSOC, NOC, and Fusion Center concepts with organizations or through Managed Security Service Providers (MssP, MSP, MDR).
It makes little sense to build walls and towers around the castle and then have no sentries to man them or insufficient sentries to be adequate. In this sense, all architectures must be right-sized operationally and fit for purpose, or they will not be effective regardless of how many tools are thrown at the business problem.
Anyone can use this public domain document and modify it to suit their needs.
Secure Design Principles-Reference Architecture
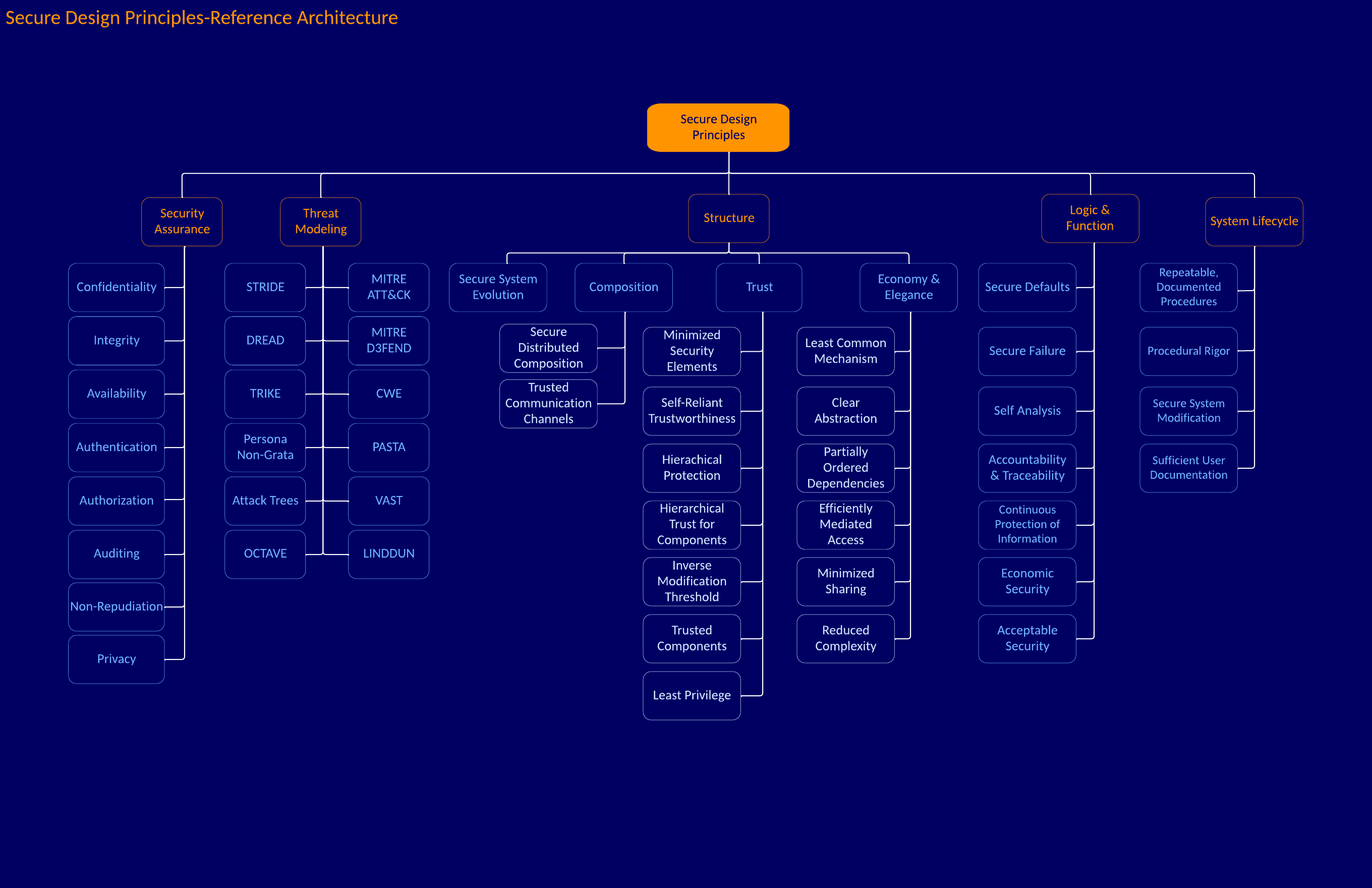
According to the Merriam-Webster dictionary, a principle is:
- a comprehensive and fundamental law, doctrine, or assumption
- a rule or code of conduct
- the laws or facts of nature underlying the working of an artificial device
- an underlying faculty or endowment
The modern secure design principles are presented in varying forms across various Internet resources and even within mainstream cybersecurity conversations and training. These core design principles dumb down the Design Principles for Security by Bensel et al. and NIST Special Publication 800-160 version 1 revision 1 Engineering Trustworthy Secure Systems. The mainstream view tends to focus only on these seven secure design principles (others might have ten principles):
- Principle of Least Privilege
- Principle of Separation of Duties
- Principle of Defense in Depth
- Principle of Failing Securely
- Principle of Open Design
- Principle of Avoiding Security by Obscurity
- Principle of Minimizing Attack Surface Area
Secure Design Principles provide a directive for developing a secure system’s underlying and comprehensive doctrine, assumption, and rule of conduct. Any system should adhere to these principles from design through development, testing, deployment, and during its running lifecycle. The principles should be developed from the NIST Special Publication 800-160 version 1 revision 1 Engineering Trustworthy Secure Systems. In addition, they should be extensible to account for MITRE ATT&CK and D3FEND.
Anyone can use this public domain document and modify it to suit their needs.
Policy and Harmonized Control Framework-Reference Architecture
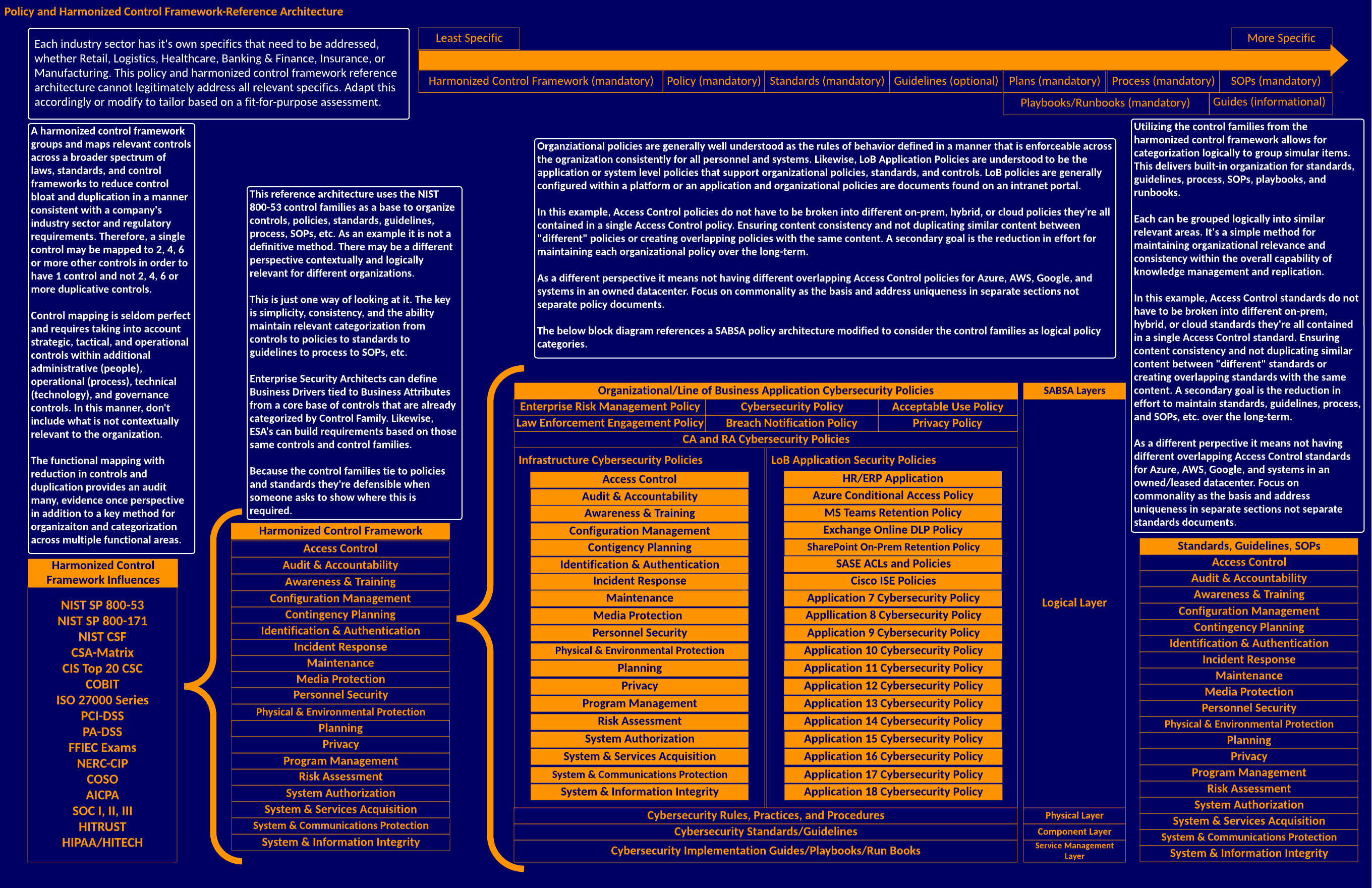
Many do not consider cybersecurity architect involvement in policy development and working with or on harmonized control frameworks. Yet, cybersecurity architecture demands the alignment of cybersecurity mechanisms with financial, IT, cybersecurity, and privacy controls related to broader regulatory compliance. If cybersecurity architects do not account for these areas, the entire cybersecurity program is in jeopardy of missing the mark in securing the overall organization. Likewise, the cybersecurity program will miss the mark on meeting regulatory compliance. Therefore, a synergy exists between cybersecurity architecture and harmonized control frameworks. Furthermore, the synergy extends outward to policies, standards, guidelines, business processes, standard operating procedures, etc., ensuring consistency under a holistic approach.
The policy and harmonized control framework-reference architecture presented is a single point of view but provides a reference from left to right for a potential direction. The reference architecture utilizes a core set of influences with the NIST SP 800-53 Rev. 4 as the base. The perspective presented is not rigid but a foundational starting point. The NIST SP 800-53 could easily be swapped out for ISO 27001, the CIS CSC v8, or the CSA-Matrix as the base. Some organizations might favor a NIST CSF direction. Adopt and adapt as appropriate to the organization relative to its critical infrastructure industry sector, market, and vertical.
The main policy architecture viewpoint is based on the policy architecture presented by SABSA in the SABSA Big Blue book (the first book listed on the Architecture My Library page) and in training from the SABSA Institute. Therefore, it is a good starting point for developing organizational and line-of-business application-level policies.
Anyone can use this public domain document and modify it to suit their needs.
SABSA is the copyright and trademark of the SABSA Institute; all rights reserved.
As a working cybersecurity professional, every attempt is made to separate professional and personal endeavors in a manner consistent with reducing conflicts of interest and maintaining ethics. Statements contained within this site are the explicit and implicit goals, objectives, endorsements, and educated opinion of the author of this site and not those of current or former employers.

