Architecture Frameworks
This Cybersecurity Architecture section focuses on an integrated architecture framework that leverages TOGAF and SABSA. A formalized architecture framework defines the framework, methodology, and practice for designing and delivering architectures. Determining the integration between business, enterprise, and cybersecurity architecture is also necessary. Likewise, architecture has integration points with the product development lifecycle.
Architecture-Domains
Regardless of the architecture framework, each relies on architecture domains. However, most focus on business, data, application, and technology as domains. At a high level, that is not inherently incorrect or wrong. Modern architectures must expand the domain model to address various aspects of cloud, on-premises, and hybrid technology deployments for business processes and digital transformation. They need to include a zero-trust strategy addressing cybersecurity threats and risks. The high-level domains (business, data, application, technology) will be developed into specific architectures by domain-specific architects, i.e., a network architect generally develops the network architecture.
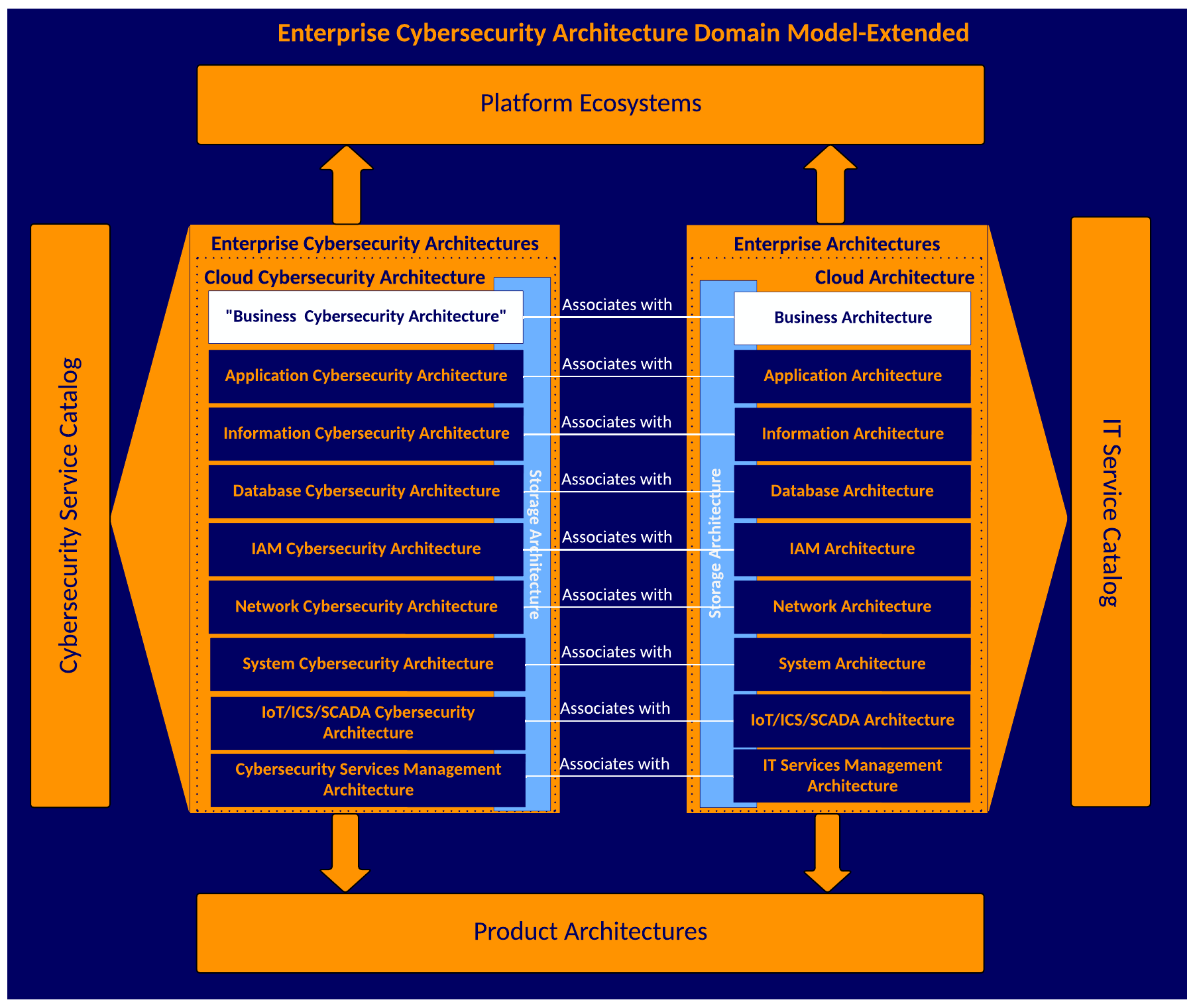
Architecture Framework
The architecture framework developed focuses on TOGAF and SABSA, but it could be redefined for SABSA and any other enterprise architecture frameworks. Although SABSA is still making inroads within the US, it is heavily leveraged in Canada, Europe, and Australia. The O-ESA has taken more of a backseat to SABSA with TOGAF integration.
This is not exhaustive but presents a singular perspective on how an architecture framework can be developed internally for an enterprise. Likewise, it level sets integration between IT, Development, and Cybersecurity to ensure cybersecurity is being addressed upfront during the architecture lifecycle versus later on or eventually having to bolt on.
This is not a conversation about building an architectural framework from the ground up like TOGAF, SABSA, or Zachman. This deployable architecture framework serves as the primary guiding framework, methodology, and practice based on TOGAF and SABSA integration.
This area is still under construction. Please be patient as I build out the documentation.
Architecture Program
An architecture framework does not exist in isolation or without the need for governance. For any architecture practice to be effective and efficient, it should be an auditable, measurable, and reportable program or subprogram. The main issue is that it should not be two separate programs or subprograms within the cybersecurity and IT organizations. These areas need to meet in the middle to address the enterprise (the whole company), corporate, and product to ensure cybersecurity is addressed upfront and not later after an architecture has been deployed.
This area is still under construction. Please be patient as I build out the documentation.
Architecture Principles
Architecture principles are those guiding statements architects leverage while designing target and transition state architectures for deployment, whether the discussion leads to strategic, segment, or capability architectures. Principles might be the essence of architecture, an essential part of design, and even a view of architectural policies. Regardless, as Greefhorst and Proper note in Architecture Principles: The Cornerstones of Enterprise Architecture, they bridge the gap between conceptual and concrete design. Architecture principles here follow their view and perspective and not the Open Group’s.
This area is still under construction. Please be patient as I build out the documentation.
Architecture Standards
Architecture standards are integrated into an architecture practice based on specific requirements, principles, and related documentation. In this instance, architects must do the leg work for Azure Well-Architected, AWS Well-Architected, OCI Architecture Framework, and Google Cloud Architecture Framework—likewise, industry-relevant standards like those from the Banking Industry Architecture Network (BIAN).
Addressing the potentially differing architecture standards across critical infrastructure industry sectors would be challenging and expensive, depending on the many required fees for membership or licensing (ISO/IEC, BIAN). This area will remain as a qualifier. Architecture standards are needed but will be addressed based on time and expenses permitted.
This area is still under construction. Please be patient as I build out the documentation.
As a working cybersecurity professional, every attempt is made to separate professional and personal endeavors in a manner consistent with reducing conflicts of interest and maintaining ethics. Statements contained within this site are the explicit and implicit goals, objectives, endorsements, and educated opinion of the author of this site and not those of current or former employers.

